Turn off Fox News for 24 hrs and educate yourself a bit!!
Reports: Liberty Reserve Founder Arrested, Site Shuttered(416)
Maybe you should post details in a forum that gives help (perhaps other users in whichever forum)
So we have been working on this for some time. We helped develop a hardening guides (heree one that directly addresses many of these issues as well as a platform that provides technical automation to help installers of these systems.
Was the Ashley Madison Database Leaked?(376)
Only after fixing any problems related to default credentials should readers consider checking for firmware updates. Some hardware makers include the ability to check for updates through a Web-based administration panel (like the one used to change the devices default password), while others may only allow firmware updates manually via downloads from the manufacturers site.
Be nice if the makers of IoT devices setup a stranded such as.
Regardless of whether your device is listed above, if you own a wired or wireless router, IP camera or other device that has a Web interface and you havent yet changed the factory default credentials, your system may already be part of an IoT botnet. Unfortunately, there is no simple way to tell one way or the other whether it has been compromised.
Cards Stolen in Target Breach Flood Underground Markets(445)
Update, 8:30 p.m. ET:Added final section with the sobering caveat that all of this hassle in changing the default passwords and updating the firmware may not actually solve the problem for many (if not all) of the affected devices.
Firmware updates can be tricky to install, because if you fail follow the manufacturers instructions to the letter you may end up with little more than an oversized paperweight. So if you decide to go ahead with any firmware updates, please do so carefully and deliberately.
Dormann said instead of hard-coding credentials or setting default usernames and passwords that many users will never change, hardware makers should require users to pick a strong password when setting up the device.
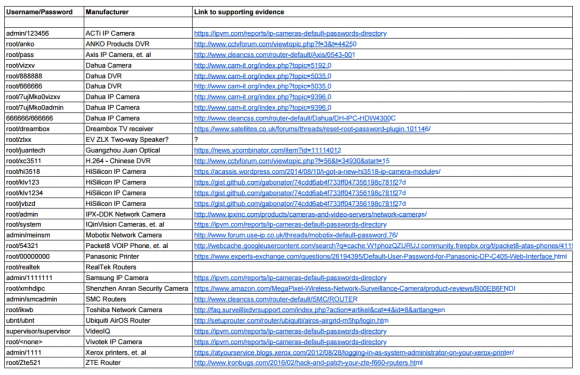
In all, there are 68 username and password pairs in the botnet source code. However, many of those are generic and used by dozens of products, including routers, security cameras, printers and digital video recorder (DVRs).
Case in point: In February 2016 I publishedThis is Why People Fear the Internet of Things, which examined a whole slew of IP cameras sold by Chinese Web camera giant Foscam that by default included a feature which would quietly phone home to a vast peer-to-peer (P2P) network run by the company. As I explained in that piece, while the Web interface for those P2P cameras included a setting allowing users to disable the P2P traffic, disabling that option didnt actually do anything to stop the device from seeking out other Foscam P2P cameras online.
gibson pages are wordy. scroll far down to link to test page.
Some readers have asked how these various IoT devices could be exposed if users have configured them to operate behind wired or wireless routers. After all, these readers note, most consumer routers assign each device inside the users home network so-calledNetwork Address Translation(NAT) addresses that cannot be directly reached from the Internet.
I dont claim to have special knowledge of each match, and welcome corrections if any of these are in error. Mainly, I turned to Google to determine which hardware makers used which credential pairs, but in some cases this wasnt obvious or easy.
As long as the password cant be reversed for example, an algorithm based off of a discoverable tidbit of information that would be a reasonable level of security. Dormann said.
Similarly, I would like to see or develop a list of Mirai-susceptible OUIs so that I can disallow those on the network.
The FCC does this with radios, NHTSA does this with cars, FTC does this for most other merchandise categories we need local and global bodies to take an active role in protecting the world from unsafely designed products.
My solution was simple. My cameras are configured to work only on my intranet, and no. PNP disabled everywhere. And just to be extra safe, through parental controls on my router, all cameras MACs are blocked from contacting internet. Then, when outside, I VPN into my network, and my camera viewer software on my phone/tablet/laptop works like Im at home. Of, course, all passwords on cameras, router, software, VPN are super long and complicated. There is no perfect security, but I think, this is as safe as I am going to get.
As a former Xerox certified tech for a Western NY VAR, I can attest that is the practice for some techs to reset the password to one of the defaults if they cant log into the printer. Sheer stupidity
Thanks for that link, Salvatore. I cant help but notice, however, that the guide instructs users to disable lots of settings in the name of security. Seems to me, a better option would be to disable the potential security risks by default, and encourage people to turn them on only if they need those features.
Then check to see if your organization is listed on Google or Shodan. If youre listed and default passwords works, time to reset your credentials for your device and prevent Internet crawlers to list your services.
Linksys wireless routers or Dell laptop wireless modems
EV ZLX 2-way speakers have zero network connectivity.
Still trying to figure out what software was running on the infected devices. Was it windows 10 IoT, a linux or some aruidino software.
(And I dont recomendation any of those courses of action)
True Goodbye: Using TrueCrypt Is Not Secure(363)
© 2018 Krebs on Security. Powered byWordPress. Privacy Policy
Even behind a NAT with UPnP off, a device can be infected by Mirai-like malware running on a PC, smartphone or any other capable host within the LAN.
eBanking Best Practices for Businesses
My advice for those running devices with the default credentials? First off, make sure you know how to access the devices administration panel. If youre unsure how to reach the administration panel, a quick search online for the make and model of your device should reveal an address and default credential pair that can be typed or pasted into a Web browser.
Following the Money, ePassporte Edition(353)
There are numerous professional speakers that connect using Dante and AES50 over Ethernet but the EV ZLX series definitely does not.
Which is part of the problem, saysWill Dormann, senior vulnerability analyst at theCERT Coordination Center(CERT/CC).
More useful would be a list of devices which arent as vulnerable to Telnet & SSH attack. Anybody got one?
As KrebsOnSecurity observed over the weekend, the source code that powers the Internet of Things (IoT) botnet responsible for launching thehistorically large distributed denial-of-service (DDoS) attackagainst KrebsOnSecurity last month has beenpublicly released. Heres a look at which devices are being targeted by this malware.
This would stop most botnets from crawling the net looking and logging into the devices with known/default user/PWs successfully
Sextortion Scam Uses Recipients Hacked Passwords(348)
Whoever did this should be prepared to face legal repercussions.
Brian Karas, a business analyst withIPVM a subscription-based news, testing and training site for the video surveillance industry said in his experience often times IP camera users can change whatever settings they want in the devices Web interface, but thats no guarantee the changes will affect how the device can be accessed via Telnet or SSH.
What makes the IoT attack vector unique is that theres no incentive for anyone to fix it. How much do *YOU* care that your fridge just broke the internet? Probably not that much, definitely not enough for you to change your fridges admin credentials, update firmware, etc.
For example, a compromised laptop could infect WiFi cameras at a coffee shop it is briefly used in. (That is, if that coffee shop has a plain vanilla WiFi LAN.)
Who Makes the IoT Things Under Attack?
The trouble is, even if one changes the password on the devices Web interface, the same default credentials may still allow remote users to log in to the device using telnet and/or SSH.
Those Ubiquiti passwords are used on all of their devices that Ive seen. That includes at least their p2p links and cameras. Ive seen multiple nanostation and aircams using that same pair.
Link to Gibsons test page is wrong; goes to a local Windows confit utility instead of his ShieldsUp scanner.
However, the solution to eliminating and preventing infections from this malware isnt super difficult. Mirai is loaded into memory, which means it gets wiped once the infected device is disconnected from its power source.
Maybe those are susceptible, if those have telnet logins that are independent of logins user edits/sets in the web interface.
ExxonMobil Bungles Rewards Card Debut
Tags:CERT Coordination Center,CERT/CC,IoT,IPVM,Mirai botnet,mirai source code leak,Will Dormann
Theres one solution but its gnarly and quite illegal. Have cameras /(etc) that have public exploitable vunls start perma DDOSing their manufacturers. You can bet your bottom dollar those manufacturers will be incentifvised to fix it when there very existence as internet citizens is at stake.
Indeed, according tothis postfrom video surveillance forumIPVM, several IoT device makers includingHikvision,Samsung, andPanasonic have begun to require unique passwords by default, with most forcing a mix of upper and lowercase letters, numbers, and special characters.
I know what he means though. This short list just happens to be the ones used in this attack on some of the low-hanging fruit. Next time it could easily be Telnet or SSH used and your really complex password will make no difference. I need to set up a DVR for CCTV cameras in an office and a requirement is they want to be able to see live footage on the web if the alarm goes off. Any advice on buying and configuring kit that isnt leaving them wide open?
Thanks, Michael. As I said in the story, these should not be taken as gospel. I will go back and look to see if I have the link to supporting evidence, but if you have found another candidate, Id be happy to update the graphic.
When we elect a known criminal to public office who has deliberately compromised security to cover their own tracks while shaking down foreign governments and corporations how can we punish anyone. Legally, its selective enforcement.
Notorious Hijack Factory Shunned from Web
Interestingly, Karas said hes been pressing Dahua whose IoT devices are heavily represented in the above default password list to tell him how many of their devices are vulnerable. Karas said Dahua told him that although the companys newest models didnt have this problem, the company was preparing to launch a trade-in program for customers with default-insecure devices.
That seems to me to be the crux of the problem for most IoT devices: They are insecure by default, and require readers to step through a 23-page PDF on how to do that.
Its a problem of the commons and, like all public goods problems, we need a public solution.
When the device comes back online, quickly fire up a Web browser, navigate to the administration panel, enter the default credentials, and then change the default password to something stronger and more memorable. I hope it goes without saying that any passwords remotely resembling the default passwords noted in the image above are horrible passwords.Heres some adviceon picking better ones.
Sources: Target Investigating Data Breach(620)
I believe thats the default login for Ubiquiti stuff period. I know my UniFi AP used that as the default, as does the UniFi controller on first install
DJ, thats ridiculous. A list of non-affected devices (whitelist) would be huge, its much easier to read and distribute a blacklist.
Unfortunately, many of these devices also require periodic software or firmware updates to fix previously unknown security vulnerabilities that the vendor discovers or that are reported to the hardware maker post-production. However, relatively few hardware makers do a good job of making this process simple and easy for users, let alone alerting customers to the availability of firmware updates.
This isnt something that requires a lot of talent, particularly because this uses simple, well-known holes in security. Indeed, no one familiar with default security on the internet is surprised by this attack.
Did the cyberattack affect Linksys wireless routers or Dell laptop wireless modems? I help friends & family with computer problems & theres been several bricking in the last 2 weeks.
ubnt/ubnt is the default password for Ubiquiti Aircam and UniFi Video Cameras. Given the prevalence of cameras on this list I guess thats more likely the target than AirOS. Could be both, though.
I notice theres no link in the evidence column so Im confused how this device ends up on the list.
Online Cheating Site AshleyMadison Hacked(798)
There should be a global standards body for certifying the security standards of IoT hardware. Much in the same way Underwriters Laboratories certifies my light bulb socket wont set my house on fire (and without that certification, hardware store cant import that socket from China) gotta find a way to bring governments and manufacturers together worldwide to enforce security audits on consumer products
The problem is theres no hard and fast rule, Karas said. What often happens is Telnet and SSH are an operating system-level login, and the [Web interface] tends to be more of an application level login. Sometimes changing a password on one changes the password on the other, but more often the Web [interface] is completely different, and changing the password there may not change the underlying password needed to access the device remotely via SSH and Telnet, he said.
Check if linksys has firmware updates or dell has driver updates. Dell download pages have brief notes.
I examined the less generic credential pairs and tried to match each with a IoT device maker and device type. As we can see from the spreadsheet above (also available inCSVandPDFformats), most of the devices are network-based cameras, with a handful of Internet routers, DVRs and even printers sprinkled in.
Feds: hire them, dont prosecute them! Good talent is difficult to recruit, and Silicon Valley often gobbles up top tier talent for those who can make it out of moms house.
When it comes to software updates, automatic updates are good, Dormann said. Simple updates that notify the user and require intervention are okay. Updates that require the user to dig around to find and install manually are next to worthless. Devices that dont have updates at all are completely worthless. And that can be applied to traditional computing as well. Its just that with IoT, you likely have even-less-technical users at the helm.
Sextortion Scam Uses Recipients Hacked Passwords
Not that youre incorrect, Im just highlighting that it goes beyond their routers.
This entry was posted on Monday, October 3rd, 2016 at 4:17 pm and is filed underOther. You can follow any comments to this entry through theRSS 2.0feed. Both comments and pings are currently closed.
You do realize that once a packet gets routed, the MAC address changes, right? Andthere are other ways of moving data around at Layer 2 other than the usual Ethernet.
But as several readers already commented in my previous story on the Mirai source code leak, many IoT devices will use a technology calledUniversal Plug and Play(UPnP) that will automatically open specific virtual portholes or ports, essentially poking a hole in the routers shield for that device that allows it to be communicated with from the wider Internet. Anyone looking for an easy way to tell whether any of network ports may be open and listening for incoming external connections could do worse than to runSteve GibsonsShields Up UPnP exposure test.
They didnt give me a straight answer on this one, but that that tells me is they have a whole bunch of devices that may not be firmware updatable, which means they cant make those devices more secure without swapping out the underlying hardware.
The malware, dubbed Mirai, spreads to vulnerable devices by continuously scanning the Internet for IoT systems protected by factory default usernames and passwords. Many readers have asked for more information about which devices and hardware makers were being targeted. As it happens, this is fairly easy to tell just from looking at the list of usernames and passwords included in the Mirai source code.
If possible, reset the device to the factory-default settings. This should ensure that if any malware has been uploaded to the device that it will be wiped permanently. Most devices have a small, recessed button that needs to be pressed and held down for a several seconds while powered on to reset the thing back to the factory default settings.
Several readers have pointed out that while advising IoT users to change the password via the devices Web interface is a nice security precaution, it may or may not address the fundamental threat. Thats because Mirai spreads via communications services called telnet and SSH, which are command-line, text-based interfaces that are typically accessed via a command prompt (e.g., in Microsoft Windows, a user could click Start, and in the search box type cmd.exe to launch a command prompt, and then type telnet IP address to reach a username and password prompt at the target host).
If youre looking to test your devices for default username and passwords, the following sites will help you out, the following websites are great starting points:
LuminosityLink RAT Author Pleads Guilty
Even when users are interested in and looking for this information, the vendor doesnt always make it easy, Dormann said.
1) Post reset/boot of device the default User/PW is only good for say 1 hour
So whats all the fuss about? Havent we always had things on our networks? In fact, until 20 or 25 years ago most of our networks were about connecting things PCs, terminals, servers, hosts, routers, printers, etc. People were an afterthought, really.
But as I noted in Saturdays story, there is so much constant scanning going on for vulnerable systems thatIoT devices with default credentials can be re-infected within minutes of a reboot. Only changing the default password protects them from rapidly being reinfected on reboot.
Your email account may be worth far more than you imagine.
With that said , the nuclear option isnt exactly fair on the poor users. Perhaps the vigilante solution is to just remote patch the damn things
Somewhat of a long shot here but, is it possible to pull out the MAC addresses of the devices that are part of the mirai device list and see if they can be organized into a machine discernable list so that I can write an IPS signature for it. Meaning, are the Octets in the MACs of these devices in a sequential range that allows for me to create a signature on that subnet. If that works, then we can work with ISPs or others in the internet business to more easily identify aggregated traffic.
2) After that hour it default User/PWwont work and can only be logged into with a user/pass that is not same as default.
To the extent that we should consider cutting these people some slack, it shouldnt be based on talent on their part, but because of irresponsibility of those of us who designed these systems in the first place.